Custom domain and automated encryption (SSL/TLS)
If you have activated the firewall on your service ensure port 80 is open or else certificate creation/renewal will fail
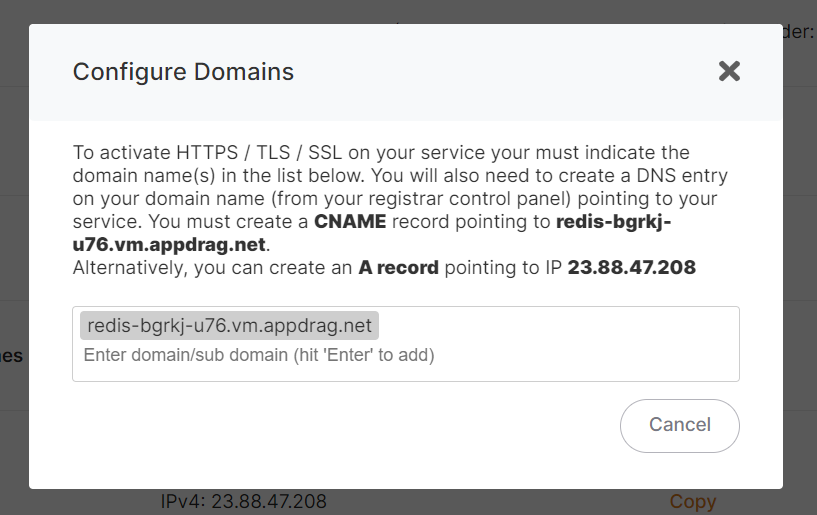
FromAccess the service"Manage dashboard,SSL clickDomains" onoption within the "Custom Domain Names"Names" row located in the overview tab thenof clickthe onservice "Manage SSL Domains"dashboard.
From there you can manage allowed domains for SSL. If you want to add a new domain, just type it and press enter to add it to the list of authorized domains. You will also need to create a DNS entry to point your domain to the IP address of your service.
You can either create an A record or CNAME record to point to your service. CNAME is preferred as it won't change even if your IP change (eg: this can happen if your clone/migrates your service to another provider.
Once added, you can verify if your DNS entry is propagated with a tool like https://dnschecker.org/
Once propagated SSL should work instantly on your service. The certificate will be automatically generated and renewed.
For some software you will also have to update an env var to indicate the domain to be used. To do that in the overview screen of your service click on UPDATE CONFIG button > Env tab > there update the domain env var with your own domain
Cloudflare users
If you are using Cloudflare reverse proxy (orange cloud icon) please check detailed instructions about Cloudflare & Elestio here:
https://docs.elest.io/books/security/page/using-cloudflare
Troubleshooting SSL not generated
You can display the nginx log with this command in a terminal:
cd /opt/elestio/nginx;
docker-compose logs -f;
press ctrl+c to stop displaying the live logs
Reset SSL_DATA folder
In some cases, the /opt/elestio/nginx/ssl_data folder can become corrupted, if this happens, connect to a terminal and try this:
cd /opt/elestio/nginx/;
docker-compose down;
mv ./ssl_data/ ./ssl_data_old/;
mkdir ./ssl_data/;
chmod 777 ./ssl_data/;
docker-compose up -d
Once executed just open your custom website url again and your certificate should be generated and your site served over SSL/TLS.