Using Cloudflare
(OLD) Cloudflare users
If you are using Cloudflare, you should not enable reverse proxy (orange cloud) on your DNS entries, or else it will prevent the SSL certificate creation/renewal process from Elestio with Letsencrypt.
If you still want to use Cloudflare with orange cloud, you should do this to disable elestio SSL for your custom domain:
1) Connect to the VM with SSH and type this:nano /opt/elestio/nginx/.env
there remove your domain from the first line and save with CTRL+X
then type this command:cd /opt/elestio/nginx;docker-compose down;docker-compose up -d;
after that nginx won't try again to obtain an SSL certificate for your domain and your site will use only the SSL from Cloudflare.
Cloudflare DNS:
If you wish to use Cloudflare for DNS ONLY, you can configure it just like any other DNS provider, and simply follow the steps for adding a custom domain as usual.
WARNING: Your domain DNS entry must have a GRAY cloud, not an ORANGE (proxied) cloud next to the entry.
![]() This is the correct image shown for DNS-only entries.
This is the correct image shown for DNS-only entries.
Cloudflare Proxy
Even though Elest.io automatically provides SSL and has a firewall, there can be advantages to using Cloudflare for Proxying traffic, notably DDoS attacks and automatic filtering of scripted attacks.
Note: Cloudflare only proxies traffic on certain ports. If you want to use this hostname for SSH, FTP, or other services whose ports are not listed in the above link, you must configure Cloudflare to provide DNS only or use Cloudflare's Spectrum offer.
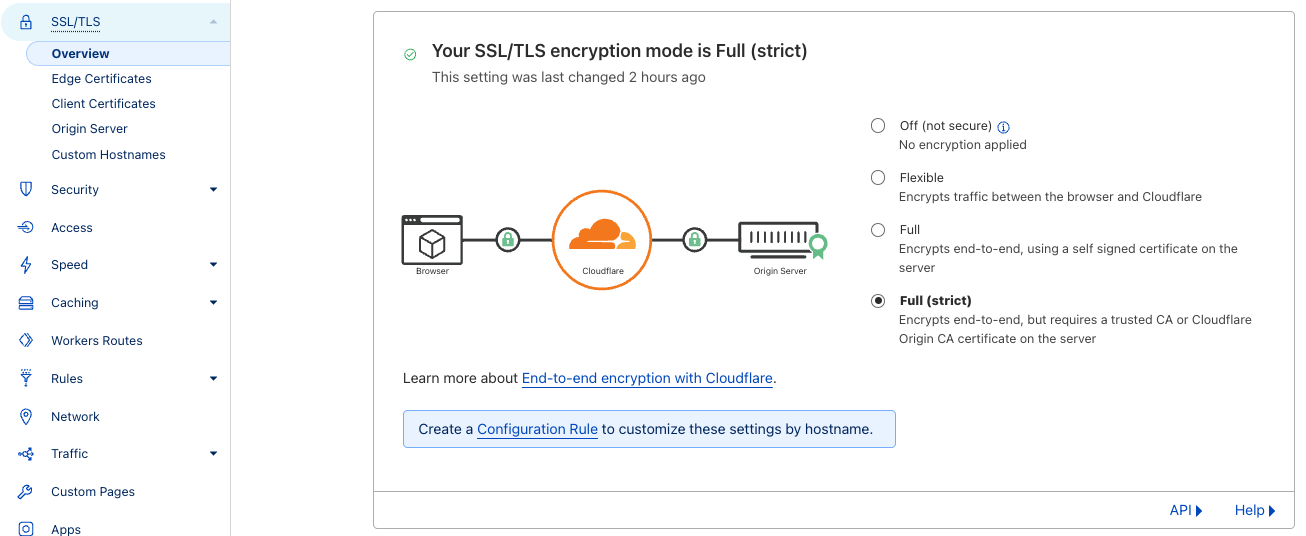
Because Elest.io already creates an SSL certificate for your website trusted by a root CA, the recommended configuration is to set Cloudflare to use Strict SSL verification when connecting to your server.
Before continuing, ensure you have already configured the domains as per the instructions on the previous page.
Option 1: To set up strict SSL verification for your whole domain:
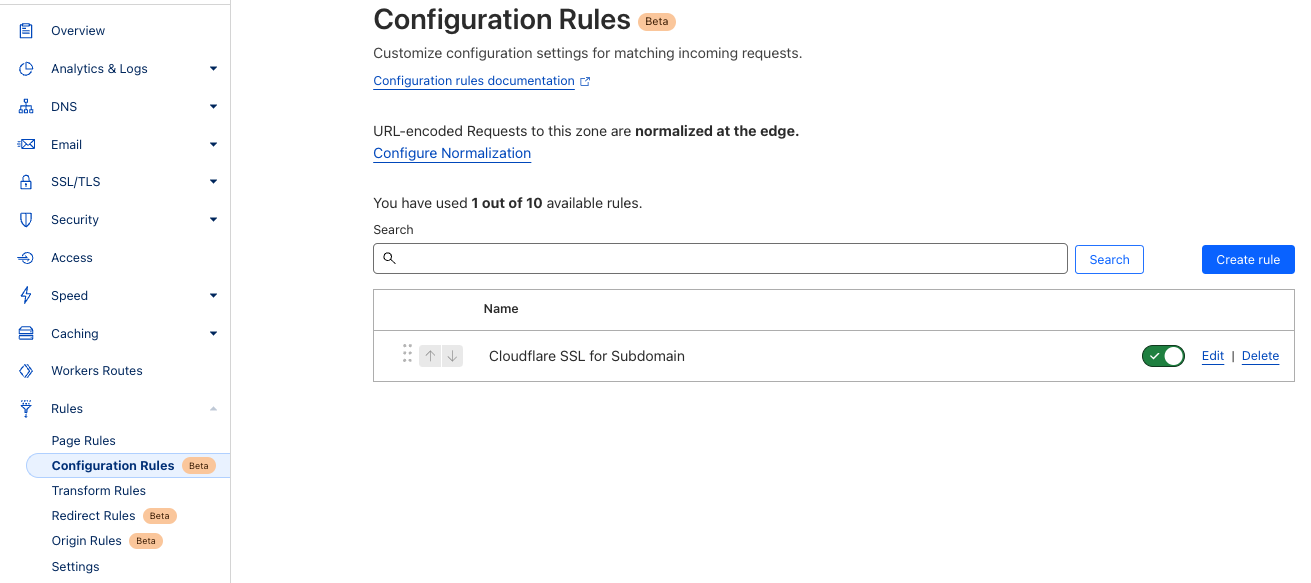
Option 2: To set up strict SSL verification for a specific subdomain:
- In your domain's dashboard, navigate to
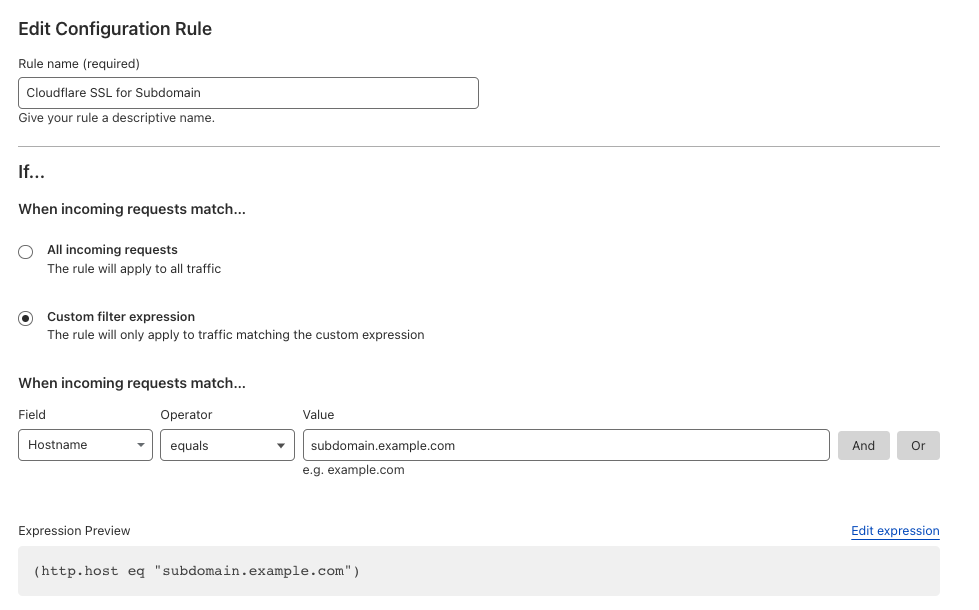
Rules > Configuration Rulesand clickCreate Rule - Name
Asand shown inconfigure the diagram,incoming thisrequest will create a secure connection between the client and Cloudflare's servers, and Cloudflare will connect securely to your Elest.io service.
If3. you are using Cloudflare, you should not enable reverse proxy (orange cloud) on your DNS entries, or else it will preventConfigure the SSL certificateto creation/renewalStrict
4. ElestioClick withSave
Option 3: Manual configuration (Advanced)
If you stillneed wanta tocustom useimplementation, Cloudflareyou can disable the creation of an SSL certificate with orangethe cloud,following steps.
These changes can be overwritten in the future if you shouldmodify dothe thislist toof disabledomains elestiovia SSLthe forElest.io your custom domain:dashboard.
1) Connect to the VM with SSH and type this:
nano /opt/elestio/nginx/.env
there remove your domain from the first line and save with CTRL+X
then type this command:
cd /opt/elestio/nginx;
docker-compose down;
docker-compose up -d;
afterAfter thatthat, nginx won't try again to obtain an SSL certificate for your domain and your siteconnection with Cloudflare will usenot onlybe the SSL from Cloudflare.secured.